About
DYNSECUCASH is a development of DYNSECUCOIN, a company that is created and managed by a group of entrepreneurs with a long standing experience in IT and other businesses.
While worldwide cash remittances companies and online platforms exist, none of them offer the unique secured ID protection that DYNSECUCASH has to protect the identity and the privacy of its members, and to prevent fraud or theft or any form of hacking and phishing and skimming, while at the same time making it very easy for the members to send and receive cash from and to any place in the world, and in such a way that no passwords or email identification is needed, and also no complex 2 way verification systems and enrollments are needed.
Internet users hear or read nowadays, on an almost weekly basis, about horror stories of stolen user ID credentials, stolen passwords, unauthorized use of their private data, and even stolen financial data. Cases of massive unauthorized data sharing, hacking, phishing and skimming, even auctioning on darknet of stolen credentials, are frequently being reported, and they happen in all corners of the world.
Hence, users want protection. Very good protection. But users don’t want at the same time the hassle of complex passwords and pin codes combined by all kinds of two-way verification and biometric verification systems, (which in the end are still not safe, since these are all so called "static" verification keys, prone to be hacked by savvy and sophisticated hackers), making it cumbersome to log in each time they want to place a simple bet or check their status and winning amounts pay-outs.
The founders of DYNSECUCASH researched and tested the unique and patented "Cognitive ID authentication" of the company NimbusID (www.nimbusid.com) and have additional own patents for additional layers, especially in the realm of decentralized block chain applications.
The benefits then for the DYNSECUCASH members are : ULTIMATE yet EASY user authentication:
- A DYNSECUCASH member can register from any online device, and does NOT need to give email or password or any personal ID element at that initial registration instance or to log in anytime.
- ULTRA SAFE ! : Once a DYNSECUCASH member is registered, he or she can log-in again, and provide safely all legally required personal ID data and financial transactions data, which are kept safely "behind the cognitive ID wall", meaning, no one else and no hacking software can access these data.
- EASY and FAST ! : Each time a DYNSECUCASH wants to send or receive cash from and to anywhere in the world: it is sufficient to find a nearby franchise and go there and authenticate from any medium (smartphone, tablet, laptop,… ) and deposit the cash to be send, or receive the cash that was sent.
Explanation about Cognitive ID authentication:
Once again, passwords, biometrics, and 2 way verification do not GUARANTEE identity. They just grant access. Access is granted based on "what you possess" not "who you are."
Biometrics and 2 way verification was supposed to solve these issues by limiting access to individuals based on difficult-to-copy credentials tied to complex physical traits like fingerprints and iris scans or face recognition or speaker’s voice verification. However, despite their complexity, these supposedly "identifying" traits are easily copied in a digital world as they are simply static credentials.
What is Cognitive Identification?
Cognitive Identification (CogID) solves this problem by eliminating static credentials. CogID operates on HOW we think, not what we KNOW. It taps into the complex relationships we create between seemingly unrelated events, people, and things in our life. And : nobody can look "inside your own memories, except you yourself, and no (hacking) software can be developed to "read" your own memories.
As an example, let’s take an imaginary, yet possible experience in my life:
"I took a cruise to Jamaica last year. On the cruise, my cabin steward was named Yuri. He folded our towels into cute animal shapes. My favorite was the elephant. While on the cruise, we had an amazing chocolate buffet one night. One chef had carved a beautiful mermaid out of chocolate. I got a piece of the fin LOL!"
That story has all the ingredients I need to implement a cognitive identification test. Step 1 is to pick out some "recognition objects." In the cognitive ID world, a recognition object is a combination of a focus object and an attribute. For example, a focus object might be "cruise." Because of my memories, I have linked numerous attributes to this focus object.
When I think of "cruise," I now automatically think of Yuri, mermaids, chocolate, Jamaica, and elephants. Someone without my experiences will not have made those mental links between those attributes and the focus object.
A good cognitive system will parse a paragraph (like the cruise story above) and create these focus objects and their attributes automatically. I would then enter quite a few more recognition objects comprising multiple focus objects having multiple attributes.
The Cognitive ID Login Process
When it is time to log in, the CogID system will randomly pick one of my focus objects. The system will surround it in a number of fake or false focus objects. Below, the system will list a number of attributes. Only ONE of them will connect with only ONE of the focus objects.
A already registered user sees the four or five recognition objects and immediately spots the legitimate one. They then look at the list of possible attributes and click the only one that is linked to their focus object.
To illustrate, during my login, the system might present me with the following focus objects: Bed, Arkansas, Cruise, Lemonade.
Below, it might give me the following attributes: December, Lathe, Bumblebee, Red, Chocolate, Squirrel.
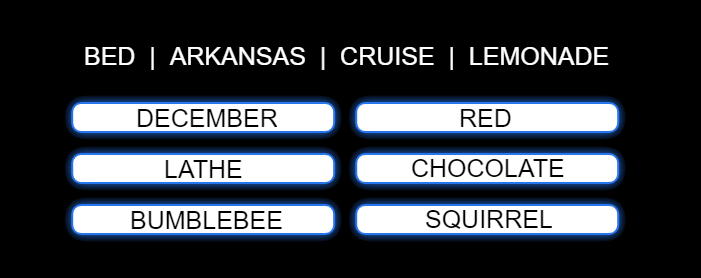
I would immediately recognize that "cruise" is my focus object, and "chocolate" is my attribute. I would click on Chocolate. Notice, I did not click on "cruise." That’s how cognitive ID thwarts those spying over your shoulder. While they may see which attribute you choose, they will have no idea which focus object it goes with, preserving the security of the link.
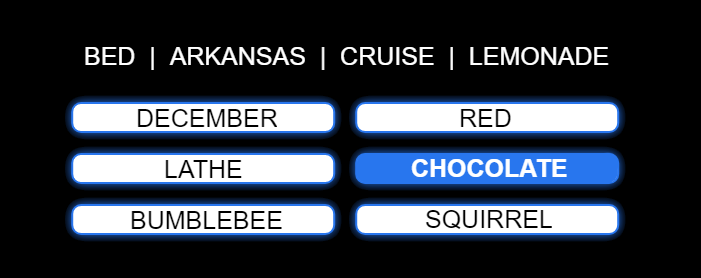
With enough recognition objects, no two logins will ever be the same. Gone are the days when you could write your password on a sticky note! A network administrator could decide how many recognition objects would have to be verified to confirm a user’s identity.
And, if someone clicks the wrong attribute, the system does not give an error. It just keeps listing recognition objects until the success threshold has been crossed. A hacker "guessing" at these attributes will have no idea which guesses were correct and which were not.
With Cognitive ID authentication, the weaknesses of passwords, biometrics, and 2 way verification are eliminated.
See Tutorial